Aqui encontrarás todos los puntos que se han tocado en los articulos 😉.
📌 Active Directory
On this machine we compromised an Active Directory domain.
📌 BufferOverflow
CTF challenge about a system intrusion
📌 Bug Bounty
Some Resources to apply in a bugbounty
📌 CTF
CTF challenge about a system intrusion
📌 CVE
CTF challenge about a system intrusion
Linux machine medium level
📌 Devops
Kubernetes is an open source software developed to manage and automate the operation of container virtualisation tools.
📌 GTFOBINS
📌 HTB
Linux machine medium level
Linux machine medium level
📌 Intrusion
CTF challenge about a system intrusion
📌 Linux
Linux machine medium level
Linux machine medium level
📌 Payloads
JSON Web Tokens (JWT) are a format for sending cryptographically signed JSON data between systems. In theory, they can contain any type of data, but are most commonly used for...
Cross-Origin Resource Sharing (CORS) is a browser mechanism that allows controlled access to resources outside a given domain. It extends and adds flexibility to the same-origin policy (SOP). However, it...
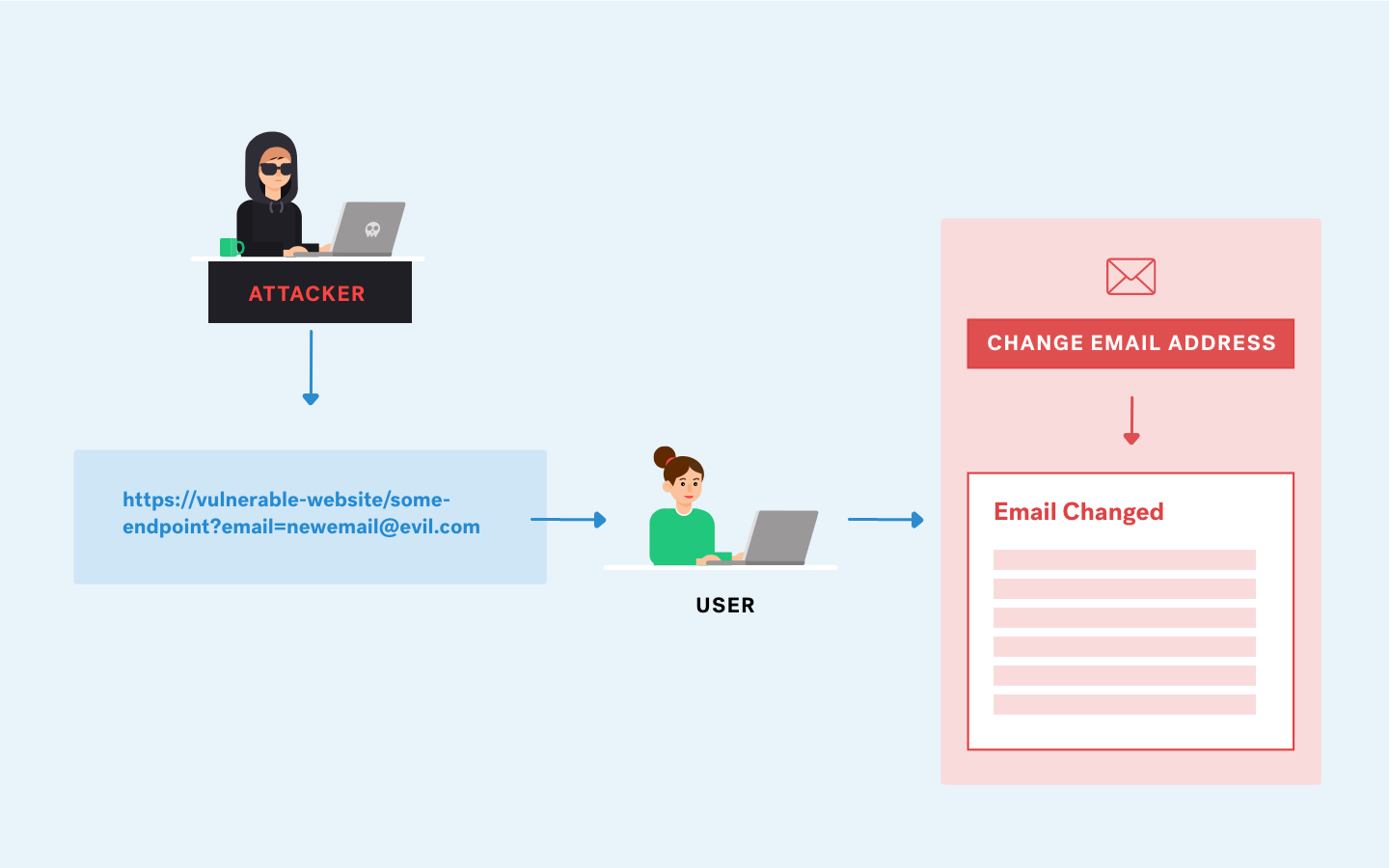
CSRF attacks (Cross-site request forgery) is a type of malicious exploit that aims to perform unauthorized operations that will be executed by a user that the website trusts.
XXE (XML External Entity) attacks are vulnerabilities that arise in applications that parse XML input. Thanks to this an attacker could alter the XML data in the request to execute...
📌 Red Team
On this machine we compromised an Active Directory domain.
📌 Resources
Some Resources to apply in a bugbounty
📌 SMTP
CTF challenge about a system intrusion
📌 VNC
Linux machine medium level
📌 Web Security
JSON Web Tokens (JWT) are a format for sending cryptographically signed JSON data between systems. In theory, they can contain any type of data, but are most commonly used for...
Cross-Origin Resource Sharing (CORS) is a browser mechanism that allows controlled access to resources outside a given domain. It extends and adds flexibility to the same-origin policy (SOP). However, it...
CSRF attacks (Cross-site request forgery) is a type of malicious exploit that aims to perform unauthorized operations that will be executed by a user that the website trusts.
XXE (XML External Entity) attacks are vulnerabilities that arise in applications that parse XML input. Thanks to this an attacker could alter the XML data in the request to execute...
📌 Wifi
📌 Wireshark